What is a VPN? Virtual Private Networks 101

A VPN (Virtual Private Network) protects your connection while you’re using the internet. It makes your browsing private, hides your IP (Internet Protocol) address and ensures your internet service provider (ISP) doesn’t track you.
In a nutshell, a VPN:
- Helps you to stay secure when using public Wi-Fi hotspots.
- Masks your IP (Internet Protocol) address.
- Encrypts your internet traffic, making your browsing more secure and private.
- Allows you to access more internet content and bypass restrictions such as government censorship.
- Ensures that your internet traffic isn’t tracked and recorded, later to be sold by your internet service provider (ISP), ad brokers, or snoops.
How does a VPN work?

A VPN like Surfshark works by routing your device’s internet connection through your chosen VPNs private server rather than your internet service provider (ISP).
By doing so, a VPN changes your visible IP address. A VPN makes it appear as if you’re browsing from the VPN server’s location instead of your device.
That’s why you can appear virtually anywhere in the world using a VPN! This feature greatly improves your privacy and is one of the two primary reasons that make a VPN so useful. The other one is security. Let’s talk about it.
How a virtual private network secures your traffic
The blind post office analogy:
Imagine a post office that doesn’t know your first or last names or address. The post person inside this office receives and sends letters containing only one piece of information about you – your customer’s ID. The post office generated this ID especially for you and it keeps it confidential.
When you receive a letter, the post person identifies you using this ID and forwards the mail directly to you. All this happens through a super-secret pipe that connects your house and the office.
In the same way, you can ask this courier to send a letter to anyone in the world. The courier will take your letter, attach your customer ID to it, slap the post office’s address on it, and ship it. As far as the receiver is concerned – the letter came from the post office and not from you (unless you signed it).
To protect the contents of the mail and your ID, these letters are translated into a language only you and the post person can understand. So even if anyone got hold of your mail – they couldn’t read it.
The technical explanation:
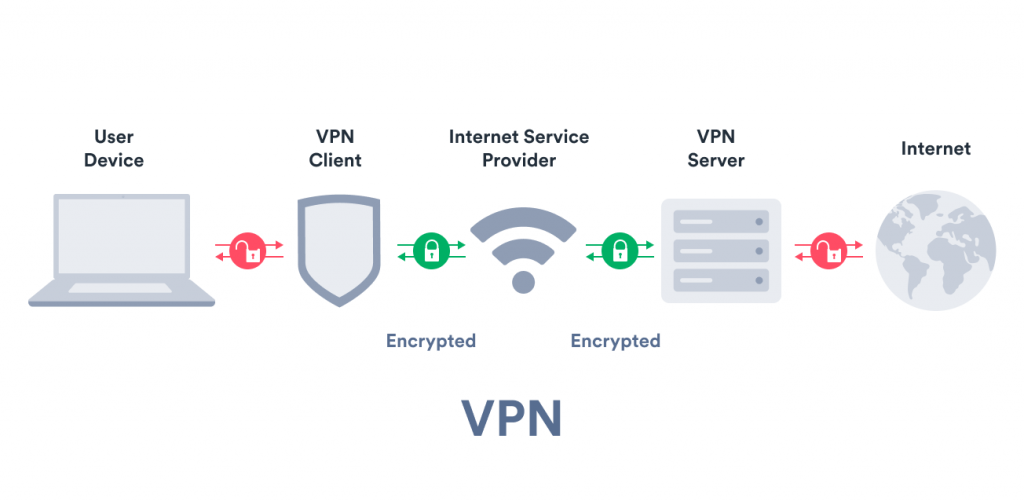
An internet connection secured by a VPN
When you connect to the internet via a VPN, it establishes a secure virtual tunnel (i.e., a secure connection) between itself and one of its servers. This tunnel is then used to transfer all of your internet traffic originating from your apps and websites.
But the VPN connection goes a step further. To ensure the tunneling process is secure, the VPN client and the VPN server encrypt your data (English: turn into scrambled, unreadable code) using a shared key (more about this below).
The VPN client and the VPN server do this every time data travels through the encrypted tunnel. This way, no one can snoop on your traffic. When the data passes through – it’s rearranged again, i.e., decrypted into readable text.
This way, a VPN ensures that your IP address, location, and online identity remain hidden from your internet service provider and third-party websites.
What is a VPN server?

So I’ve mentioned VPN servers several times now, but what are they? Are they any different than regular servers?
Well, not really. A VPN server is just a standard server configured with VPN software. This ensures that only people with VPN client software can connect to it.
If you try to connect to a VPN server it will ask for authentication (proof) that you have a VPN client. Once you’re in, all your traffic goes through this server. To anyone watching from outside, they can only see a mess of random internet data going in and out of the server. Hence, your whereabouts remain unknown.
So, what can a VPN do for you?

Still following? Great. We’ve covered the basics of how a VPN works. Now, let’s take a look at what all that technical mumbo jumbo means for you!
- A VPN protects you on public Wi-Fi
Free public Wi-Fi may be handy if you’re on the go. Sadly, it is really unsafe and makes you vulnerable even to basic cyber attacks. A VPN encrypts your online data and helps secure your personal information when you use Wi-Fi in airports, coffee shops, or other public places. It’s useful for hiding your web activity when you want to access sensitive information in public like online banking, emails, or crypto assets.
- A VPN masks browsing and torrent history
Masking your IP address is essential to secure online privacy. A Virtual Private Network ensures that your location, browsing habits, and torrenting history aren’t directly linked to your identity. This way, you can surf with peace of mind without any third parties trying to steer your choices.
- A VPN unlocks blocked and censored websites
Access to various websites is restricted in many countries due to geo-blocking and censorship. You can unblock sites by connecting to a VPN server based in a different country. This allows you to bypass internet censorship and various geo-restrictions for content, social media, whistleblowing, or even research purposes.
- A VPN helps stream Netflix privately
With a VPN, you can remain safe when streaming Netflix and using other streaming services like Hulu, Disney+, HBO Max. Our ultra-fast servers and unlimited bandwidth will ensure a throttle and buffer-free experience. This way, you can always stay private when streaming your favorite shows and movies! Learn more about VPN streaming here.
Disclaimer: Surfshark does not encourage using a VPN in any way that would potentially violate the Terms of Service of streaming service providers.
- A VPN helps you avoid price discrimination
Websites and services use your location and cookies to tailor prices for their goods and services. With a Virtual Private Network, you can avoid such marketing practices and save a buck when shopping online or buying airplane tickets.
Browsing without a VPN: what makes your data valuable?

When surfing the web, you constantly send and receive data packets. These packets contain your IP address because they need to know where to go and come back.
Without a Virtual Private Network, your Internet Service Provider (ISP) and websites can see where these packets travel and what data comes with them. This allows them to monitor, log, and later sell this information.
Why do they care? Your data is valuable to ad brokers and other service providers because it reveals patterns in your actions, such as likes, hobbies, and interests. This can later be used to make product offers you’re more likely to buy.
The amount of information these companies collect and store has also become a privacy hazard. Data breaches happen all the time, affecting billions every year.
All that information eventually ends up on the dark web. This can lead to mass phishing campaigns and even identity theft. So, it’s better to protect your privacy and data in the first place!
What is an IP address, and why can others see it?
An Internet Protocol (IP) address is a digital label used to achieve communication between networks. It serves the purpose to identify:
- The host (you);
- Your location in the network so that it knows where to send you the information.
This means that without a VPN, the data packets traveling over the internet display your IP address at all times. It is visible to most online services, allowing websites to gather information about you.
A VPN hides your IP address and location in the process because you’re technically accessing the internet through a VPN server. And this server is where information goes before it gets encrypted and reaches you through a trusted tunnel.
Does a VPN make you anonymous?

No, a VPN does not make you anonymous. And don’t believe anyone who’ll tell you otherwise.
Let’s set one thing straight, no sugar coating – internet anonymity is a fantasy. Yes, you’ve read it right. There is no real way you can be anonymous on the web.
However, a VPN enhances your online privacy greatly. Here’s a table illustrating what a VPN does and doesn’t do:
|
With a VPN
|
Without a VPN
|
|
|---|---|---|
|
IP address
|
|
|
|
Location
|
|
|
|
Browsing habits
|
|
|
|
Internet traffic
|
|
|
|
E-mail you use to register
|
|
|
|
Credit card information used for purchases
|
|
|
|
Googling when signed in to your Google account
|
|
|
|
Information you put on social media
|
|
|
|
Targeted ads
|
|
|
What a VPN does and does not hide
In other words – there’s no cure for being careless. A VPN can help you prevent being tracked, but it doesn’t help you if you display your information openly on the web. So, be mindful of what you reveal about yourself!
What is encryption, and how does it work?
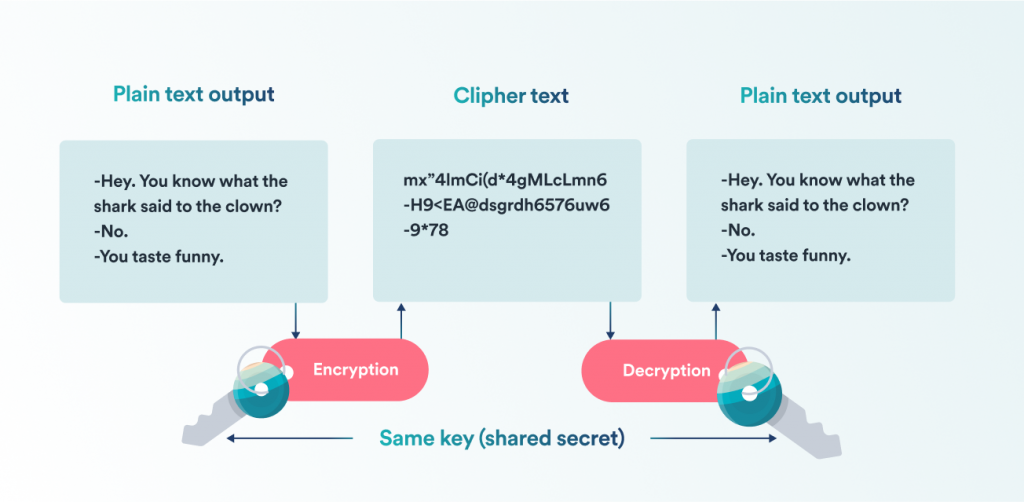
An encryption process visualized.
I’ve mentioned encryption several times already but let’s take a look at how it works.
Encryption is what VPNs use to encode and secure your data. To anyone else, an encrypted message would look like complete gibberish unless they had a shared key to decipher it.
The VPN client and server generate and exchange this key when you first connect to a VPN.
Every time your data travels through the encrypted tunnel – it’s scrambled and later unscrambled using this key.
So how powerful is encryption? Well, it depends on what encryption algorithm you use and the VPN protocol (discussed below) you pair it with.
The AES 256-bit cipher is considered the best encryption algorithm used by the US government, the NSA, and the more reliable VPN service providers, including Surfshark.
So, how secure does this make a VPN?
Short answer – Very secure.
Long answer – It gets more interesting.
Most security measures bank on making themselves too tedious to crack. For example, an encrypted session could take up to trillions of years (depending on the computer used) to decrypt by trying to “brute force,” i.e., guess the right key.
And even if someone managed to crack it, many VPN providers like Surfshark have implemented something called Perfect Forward Secrecy (PFS). This means that a VPN client generates a new key every set amount of time (about 7 minutes).
With PFS in place, cracking an encrypted session would only reveal what happened during those 7 minutes. After a new key is generated, you’d need to crack it again.
In other words – scammers and hackers wouldn’t bother cracking an encrypted connection. They prey on people who don’t protect themselves online and on public Wi-Fi hotspots.
VPN protocols
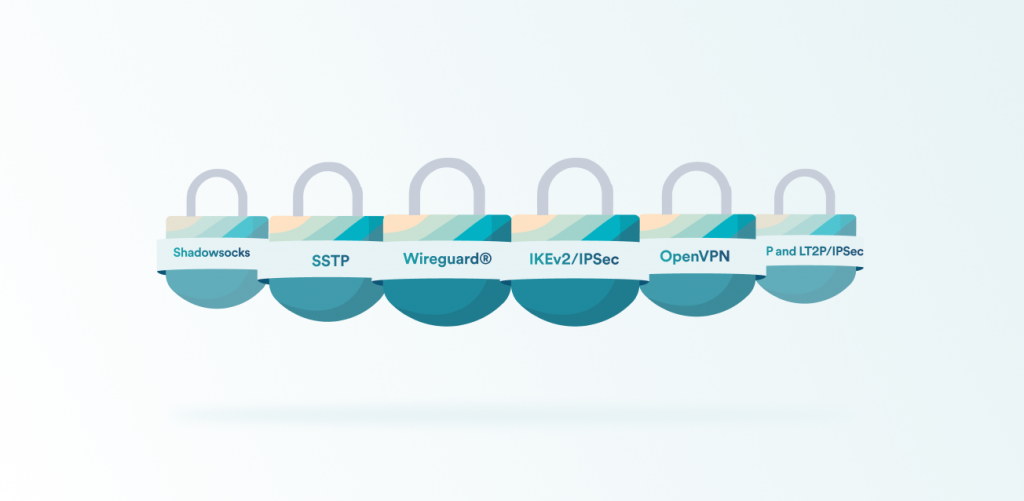
An important part of VPN security is protocols. They make your connection to the VPN server possible. They are sets of rules that determine how your VPN connections work from start to finish.
Contrary to popular belief, a VPN protocol does not have a huge impact on the speed, stability, and security of your connection. However, protocols can prove useful in different situations and will perform differently for every device! Here are some that you may come across:
- OpenVPN
OpenVPN is an open-source VPN protocol. It’s fast, secure, and compatible with many routers. Because it is open-sourced, its code has been examined through and through by cybersecurity experts worldwide. Generally, it performs worse than IKEV2 and Wire Guard.
Available on: Windows, macOS, Android, iOS, Linux, and BSD.
- Wireguard®
Wire Guard® is a relatively new protocol built to surpass OpenVPN and IP Sec in power use and performance with only 4,000 lines of code.
Available on: Windows, macOS, Android, iOS, FreeBSD, NetBSD, OpenBSD, and others.
- IKEv2/IP Sec
Internet Key Exchange version 2 (IKEv2) is on par with Wire Guard’s quality. It can outperform other protocols in terms of speed when switching networks and at shorter distance connections, making it popular among mobile users.
Available on: Windows, macOS, Android, iOS, Linux, Blackberry, Unix, and others.
- PPTP and LT2P/ IP Sec
Both are severely outdated tunneling protocols, and I highly recommend avoiding them. Albeit fast, they can offer neither the security nor reliability of OpenVPN, IKEv2, or Wire Guard.
Available on: Windows, macOS, Android, iOS.
- SSTP
SSTP is a tunneling protocol rather than a VPN protocol, meaning that it lacks the functionality of OpenVPN, IKEv2, and Wire Guard. While considered relatively safe and easy to use, its code was never audited, and it has issues working on other operating systems like Mac OS.
Available on: Windows, Linux, BSD.
- Shadow socks
Shadow socks is not a VPN protocol but a tunneling proxy. However, it can run as a protocol on VPN clients. It was created for the sole purpose of bypassing The Great Firewall of China. It is fast, hard to detect, and can be used to skirt government-imposed censorship.
Available on: Windows, macOS, Android, iOS, Linux.
How to pick a VPN service
Let’s say, hypothetically, that I have touched your soul so far (a writer can dream), and you have decided that you need a VPN.
Even then, before choosing a VPN service provider, there are important things to look out for:
- Server coverage. A strong VPN provider should have good worldwide VPN server coverage. This will give you more locations to choose from and will decrease server load.
- VPN encryption. A secure VPN encryption algorithm is essential. Make sure to look for the AES-256 cipher – a current standard in the industry.
- Server load. If there aren’t enough servers to balance the user load, connection speeds will suffer and become slow.
- VPN protocols. Protocols are vital to a VPN’s security, and you can use different ones according to which one you prefer. I recommend you look for services that offer OpenVPN, IKEv2, or WireGuard.
- Multi-hop is a VPN feature that directs your traffic through several servers at the same time. It is not essential but can give your online security an extra kick.
- Obfuscated VPN servers. When obfuscated (a fancy term for making something obscure), a VPN server will make your traffic seem like regular internet traffic. This helps to bypass VPN blockers and win at hide-and-seek against your internet provider.
- Device support. Before purchasing a VPN, make sure it supports the device that you wish to secure. It happens. We’ve all been there.
- RAM-only servers are becoming a staple for any VPN service. When running on RAM, servers automatically wipe all the data whenever turned off.
- The Privacy Policy is one of the most important parts of any VPN service. It’s an immediate red flag if your VPN provider does not have a Privacy Policy or if they’re logging sensitive information without any stated reason.
How to set up a VPN
Setting up a VPN couldn’t be easier. We recommend downloading native apps, but you can always opt for a manual setup if you’re more tech-savvy.
For a more detailed guide, check out our article on How to set up a VPN on any device.
What is a no-logging or a no-log VPN?

No-logging means handling user’s personal data without keeping any logs or records of their online activity.
In short, a no-log VPN will not collect the following information about your internet activity:
- Your IP address
- Your network traffic
- Your browsing history
- Your bandwidth information
- Connection timestamps
- Session information
This way, it ensures that you can secure your online connection and surf the internet with peace of mind.
And speaking of surfing with peace of mind, you are now armed with the knowledge to take your online privacy into your own hands.
Surfshark is a VPN with all the features mentioned in this article and we constantly strive to deliver the best user experience.
And if you want to learn more about Virtual Private Networks, security, and privacy, check out our blog for more cybersecurity content.




